That is why we have chosen to provide our customers with a vision that allows them to understand and improve their cyber posture from a broad perspective.
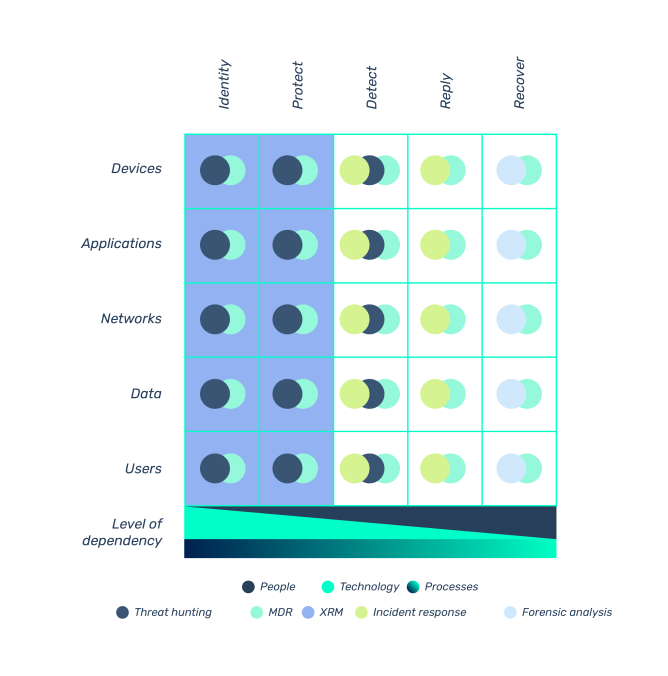
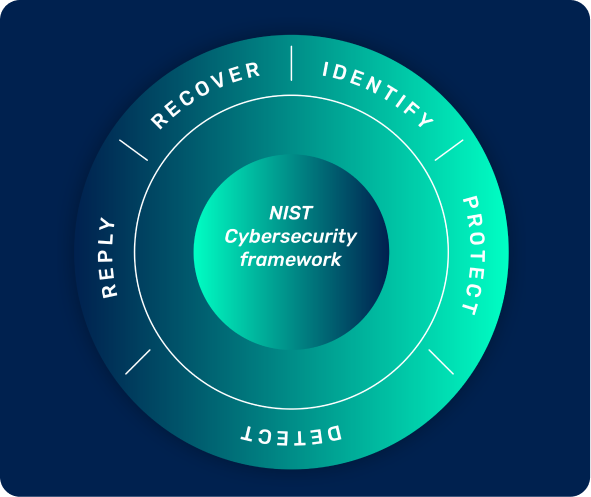
Defense functions:
identify, protect, detect, respond, recover.
Security layers:
users, data, networks, applications, devices.
PROCESSES
We support our clients with services that strengthen organizational processes through consulting, analysis, training and support personnel with the highest international standards:

Concientización

Oficial de Seguridad como servicio

Definición y/o implementación SGSI / BCP / BCP-DRP

Análisis GAP ISO 27001 / ISO27005

Awareness

Security Officer as a service

ISO 27001 / ISO27005 GAP Analysis.

ISO 27001 / ISO27005 GAP Analysis.

ISMS / BCP / BCP-DRP definition and/or implementation

Security Officer as a service

Awareness
REVIEWS
Public Sector Company

«CCD´s human talent is competent and focused on satisfying the client’s needs. Values such as responsibility, respect, commitment, and proactivity prevail among them. Thank you for the constant and timely support we have received during the extent of our commercial relationship».
Non-profit Sector Company

«I wanted to express my gratitude for all the support provided in the vulnerabilities project. I was very satisfied with the work we did together.»
Defense Sector Company

«The FireEye tool (Trellix) has made significant contributions to the detection and prevention of various types of malware, particularly ransomware attacks. Similarly, in detecting Command and Control IPS. In terms of support, they have been very efficient when it comes to responding to an incident. In the year 2023, CCD has demonstrated a great commitment to their service.»
Education Sector Company

» The University has benefited from increased visibility and specialized and detailed management of events and potential security incidents, reducing the number of false positives and focusing attention and remediation efforts on the assets that are actually affected.»
PEOPLE
Our Threat Hunting service, aligned with the NIST model, is a comprehensive solution designed to protect organizations from today’s cyber-attacks.
CCD’s team of analysts utilize the most advanced detection and extended response tools, integrating as many sources of information as possible to build a large repository of data and generate high-value research for our clients.
Our proactive approach to threat hunting, combined with our ability to respond quickly to incidents, enables our clients to reduce the time it takes to detect and respond to cyber-attacks, minimizing the impact on their operations and reputation.
When you see a security incident in the world, what argumentos do you use to answer the questions: “How secure am I?” or “How likely is it to happen to my organization?” Our Extended Risk Management (XRM) service enables you to answer these questions and communicate your risk status in a clear and concise manner, so that specific mitigation actions and decisions can be taken to ensure that the company’s risk level remains within acceptable levels.
Our approach, based on the NIST Risk Management Framework (RMF), provides a flexible operating model that, combining the knowledge of expert consultants and leading vulnerability detection technologies, adapts to each customer’s specific needs to provide and accurate measure of cyber risk while minimizing the operational load by up to 97%
Our Managed Detection and Response (MDR) service is at the forefront of cyber protection, providing organizations with the essential cyber intelligence capabilities they need.
Consistent with the NIST framework, our solution goes beyond traditional automated detection. We use advanced technologies and behavioral analytics to proactively monitor and respond to threats in real time.
Our managed approach ensures immediate incident response, identification of anomalous patterns, and consistent application of security best practices. By relying on our MDR service, organizations strengthen their cybersecurity posture, mitigate risk and proactively protect their critical digital assets.
The attack landscape continues to grow. Most threats are orchestrated by organized cybercrime enterprises from the deep & dark web, making it difficult for security teams to take action and extract relevant information in a timely manner.
Our Cyber Intelligence service is designed to take the complexity out of threat investigation and deliver immediate value by uncovering cyber criminals targeting your organization.
As part of the service, we provide proactively generated alerts on malware, potential TTPs threatening the organization, phishing scams, and brand-damaging information, including the ability to “de-register” malicious campaigns as quickly as possible.
Cyber attacks are a growing threat to organizations of all sizes. Attacks can cause significant damage to an organization’s assets, disrupt its operations, and damage its reputation.
Our Incident Response service helps organizations detect, contain, and remediate threats that may have compromised their assets. Aligned with the NIST framework, we use the best tools on the market to ensure your business continues to operate as normal.
Benefits of Cyber Incident Response service include:
- Protect organizational assets.
- Mitigate the impact of cyber-attacks
- Regulatory compliance.
Cyber Attack Investigation: with over a decade of industry experience, we are leaders in cyber attack investigation and resolution. We have helped numerous organizations identify the perpetrators of attacks and strengthen their cyber defenses.
Internal breach resolution: Our digital experts have a long track record of resolving sensitive cases of internal infidelity. We have brought clarity and justice to countless complicated situations.
Mobile Device Lab: With more than 1,000 cases resolved, our specialized Mobile Device Lab is recognized for its ability to recover critical data from damaged or protected mobile devices.
TECHNOLOGY


Devices
Organization’s technological infrastructure (workstations, servers, network equipment, mobile devices)

- EDR (Endpoint Detection and Response)
- MME (Mobile Device Management)
- Vulnerability management
- Inventory analysis


Applications
Software that supports the mission of organizations.

- Web Application and API Protection (WAAP)
- Static and dynamic code analysis
- Secure Web Gateway
- CASB (Cloud Access Security Broker)
- Email Security
- PX Forensic (Post-Exploitation Forensic)
- CNAPP (Cloud-Native Application Protection Platform)


Networking
Internal and external connectivity systems

- Perimeter Protection (NG Firewall)
- IPS (Intrusion Prevention System)
- Micro-segmentation
- Load balancers
- DNS Security
- ZTNA (Zero Trust Network Access)
- Anti-DDoS
- Network behavior analysis
- NAC


Information
Digital data, record, files, archives, documents, or any form of digital content that can be stored, processed, or transmitted over computer systems and networks.

- DLP Cloud/on Prem (Data Loss Prevention)
- Data Security
- PAM (Privileged Access Management)
- IAM (Identity and Access Management)
- Digital footprint


Users
Individuals or entities that interact with computer systems, networks, and digital resources.

- Protección Perimetral (NG Firewall)
- IPS (Intrusion Prevention System)
- Microsegmentación
- Balanceadores de Carga
- DNS Security
- ZTNA (Zero Trust Network Access)
- Anti DDoS
- Análisis de comportamiento de red
- NAC
SUBSCRIBE TO OUR NEWSLETTER:
If you would like to receive information, please register.

 Threat hunting
Threat hunting XRM Extended Risk Management
XRM Extended Risk Management MDR Managed Detection and Response
MDR Managed Detection and Response Cyber Intelligence
Cyber Intelligence IR- Incident Response
IR- Incident Response